Blog
Blog
Stay up-to-date with the latest industry trends and gain valuable insights from experts.

Imagine if your Windows 11 computer could handle tasks just like a real-life assistant. That’s the goal of Microsoft’s new…
Read More Windows 11 Gets Smarter with AI Agents: Meet Windows Agent Arena!
Feeling overwhelmed by Microsoft Teams’ chats, channels, and notifications? Good news—Microsoft is rolling out exciting updates to streamline your experience.
Read More Microsoft Teams Update: Simplify Your Workspace Today
In today’s fast-paced digital world, how confident are you in the technology that powers your business? While 90% of business…
Read More Is Your Business IT Future-Ready?
Microsoft has issued a warning to business owners about a rising phishing scam that exploits popular cloud services like SharePoint…
Read More Microsoft Warns of Phishing Scams Targeting SharePoint and OneDrive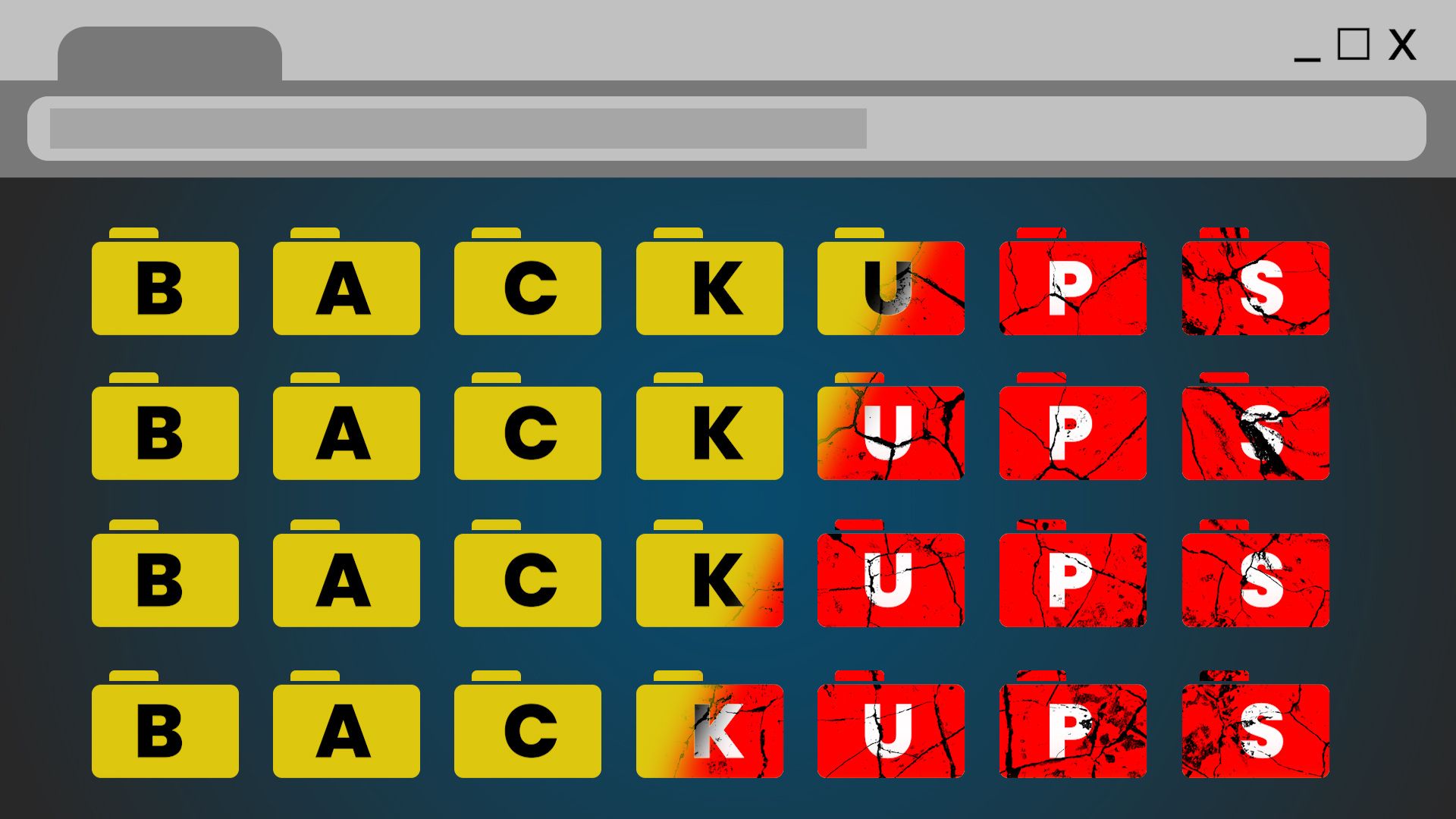
Imagine suddenly losing access to your company’s critical data, even if it’s only for a short time. It’s the stuff…
Read More Why Your Backup System Might Not Be as Safe as You Think
Windows Photos is getting an exciting upgrade in Windows 11, introducing Visual Search with Bing, a powerful reverse image…
Read More Boost Your Business with Reverse Image Search in Windows 11
With Windows 10 end of support just a year away, many business owners are asking themselves: Why haven’t we upgraded…
Read More Windows 10 End of Support is Approaching: Why Haven’t You Upgraded to Windows 11?
Microsoft recently announced that Azure sign-ins will soon require multi-factor authentication (MFA) for added security. Even if your business…
Read More Boost Business Security with a Simple Microsoft Login Upgrade
System updates can be a major hassle—slow downloads, high bandwidth usage, and storage drain. Fortunately, Microsoft is simplifying this…
Read More Microsoft: Turning 'Ugh, an update!' into 'Oh, that was easy!'
Have you heard about Team Copilot yet? It’s the latest addition to Microsoft’s suite of AI tools and should…
Read More Boost Team Productivity with Microsoft’s New AI: Team CopilotLets Get Started
We have been empowering businesses with incomparable IT support for more than two decades.